This post will explain types of ciphers. In the word of digital scams, to prevent our information, many techniques are used to keep our data safe from hackers or any 3rd party. In this article, we are going to talk about the kinds of cipher. Prior to that, lets very first see the application. Plain text is the message and data that can be legible by the sender, receiver or any third party. When the plain text is customized by utilizing some algorithms or strategies, the resulting information or message is called ciphertext. Simply put, converting plain text, i.e. legible text, into non-readable text is called ciphertext.
What is Cipher ? Types of Cipher In 2021
In this article, you can know about types of ciphers here are the details below;
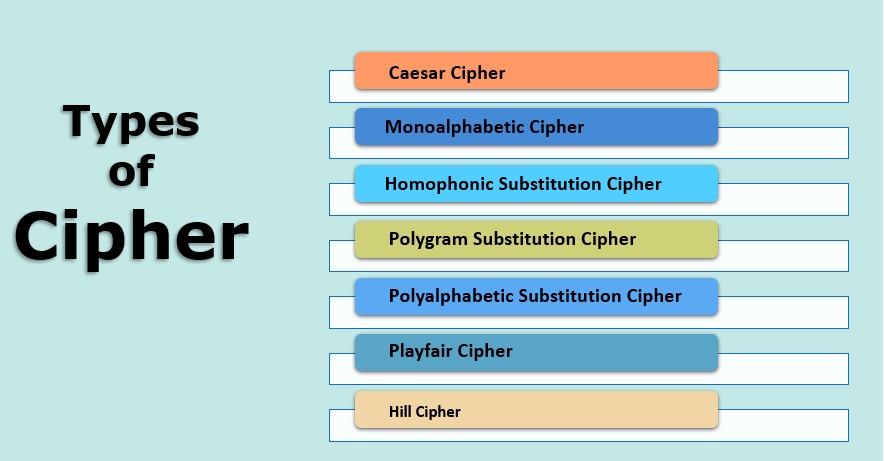
Kinds of Cipher
Numerous types of cipher are provided as follows:
1. Caesar Cipher
In Caesar cipher, the collection of plain text characters is changed by any other character, symbols or numbers. It is an extremely weak strategy of hiding text. In Caesar’s cipher, each characters in the message is replaced by three places down. Let’s see one example. The plain text is EDUCBA. As a Caesar cipher, each alphabet is changed by three-place down so that E will change by H, D will change by G, U will replace by X, C will change by F, B will change by E, and A will change by D. So here the plain text is EDUCBA and ciphertext Is HGXFED.
Caesar cipher algorithm is as follows:
- Read each alphabet of plain text.
- Change each alphabet with 3 places down.
- Repeat the procedure for all fundamentals in plain text.
A Modified Story of Caesar Cipher: This cipher works the equivalent as Caesar cipher; the only distinction is– in Caesar cipher, each alphabet is replaced with three-place down wherein a modified variation of Caesar cipher, a user decides the number to change the alphabet, and this number will be constant. For instance, EDUCBA and number for the replacement are 1, so E will replace by F, D will replace by E, U will change by V, C will replace by D, B will replace by C, and A will change by B. So here, the obvious text is EDUCBA, and ciphertext Is FEVDCB. Also check python alternatives.
A customized variation of the Caesar cipher algorithm is as follows.
– Read each alphabet of plain text.
– Take the number for replacement.
– Replace each alphabet with a defined number down.
– Repeat the procedure for all alphabet in plain text.
2. Monoalphabetic Cipher
As Caesar cipher and a modified variation of Caesar cipher is easy to break, monoalphabetic cipher enters the picture. In monoalphabetic, every alphabet in plain text can be substituted by any other alphabet other than the initial alphabet. That is, A can be replaced by some different alphabet from B to Z. B can be followed by A or C to Z. C can be replaced by A, B, and D to z, and so on. Mono alphabetic cipher triggers difficulty to break the message as there are random alternatives and a great deal of permutation and mix are available.
3. Homophonic Substitution Cipher
A homophonic alternative cipher is similar to a monoalphabetic cipher; the only distinction is in monoalphabetic, we change the alphabet with any other random alphabet except the original alphabet where homophonic substitution cipher, the alphabet is replaced by repaired alphabet or set of alphabet. The alternative alphabet is changed with te repaired. For instance, replace A with x, E with B, S with A, and so on or replace A with E, x or L, B with T, A, Z, and so on
4. Polygram Substitution Cipher
In polygram substation cipher, preferably than replacing each alphabet with different, the alphabets’ Block is changed with another block of alphabets. Change EDUCBA with XYQLAB. In this case, EDUCBA will return with XYQLAB, however EDU can be replaced with another set of the block, let’s presume EDU will change with LOD. In this kind of ciphers, plain text replacement is done within the block by block instead of character by character.
5. Polyalphabetic Substitution Cipher
Polyalphabetic Cipher is likewise referred to as Vigenere Cipher, which Leon Battista Alberti invents. In Polyalphabetic Substitution, Cipher is a technique of encrypting alphabetic texts. It utilizes multiple alternative alphabets for encryption. Vigener intersection or Vigenere table is used to secure the text. The table consists of 26 alphabets written in different rows; each alphabet is cyclically shifted to the left according to the previous alphabet, comparable to the 26 possible Caesar Ciphers. The cipher utilizes a various alphabet from among the rows at numerous points in the file encryption procedure.
Let’s think about Original text is Educba, and the keyword is Apple. For the file encryption procedure, E is coupled with A, the very first letter of the original text, E, is coupled with A, the first letter of the secret. So use row E & column A of the Vigenère square, which is E. Similarly, for the 2nd letter of the initial text, the second letter of the secret is utilized, the letter at row d and column p is s. The rest of the initial text is enciphered in the same way. The last encryption of Educba is Esjnfa. Also check angular alternative.
6. Playfair Cipher
Playfair cipher is likewise called Playfair square. It is a cryptographic method that is used o encrypt the data. The Playfair cipher process is as follows:
– Creation and population of the matrix.
– Encryption process.
Let’s talked about the above-mentioned steps in information way development and population of the matrix. It utilizes a 5 * 5 matrix to save the keyword or the secret, which is used for the encryption and decryption process.
This step is working as follows.
- Go into the keyword in the matrix in a row-wise manner, i.e. from left to right and leading to bottom.
- Skip the duplicate words in the keyword.
- Fill the staying spaces with the rest of the alphabets (A– Z) that were not a part of the keyword.
Keep in mind: while doing so, integrate I and J in the exact same cell of the table. i.e. If I or J exists in the keyword, discard both I and J while filling the remaining space encryption procedure.
The encryption procedure works as follows:
– Break the alphabets into groups (each group should contain 2 worths). The file encryption processes will be performed on these groups.
– If both alphabets in the group are the same, include x after the first alphabet.
– If both the alphabet in the group are present in the exact same row of the matrix, change them with the alphabets to their instant right, respectively. If the original group is on the ideal side of the row, then twisting around to the row’s left side happens.
– If both the alphabet in the group are present in the very same column, replace them with the alphabets instant with below, respectively. If the first group is on the rear side of the row, then twisting around to the row’s top happens.
– If both the alphabet in the group are not in the same row or column, replace them with the alphabets in the same row right away however at the other pair of corners of the rectangular shape, which the initial group specifies.
7. Hill Cipher
Hill cipher deals with several alphabets at the same time. Hill cipher works as follows:
- Appoint the number to each alphabet in plain text. A = 0, B= 1 … z = 25
- Organize the plain text message as a matrix of numbers based on the above step in number format. The resultant matrix is called a plain text matrix.
- Multiply the plain text matrix with an arbitrarily selected secret. Keep in mind that the key matrix must be the size of n * n where n means the variety of rows in a plain text matrix.
- Multiply both the matrix, i.e. action 2 and step 3.
- Determine the mod 26 value of the above matrix, i.e. matrix results in action 4.
- Now equate the numbers to alphabets i.e. 0 =A, 1 =B, and so on
- The result of action 6 becomes our ciphertext.